A week or so ago I got a call from a customer who had gone out and purchased a Linksys router "with IPSec VPN" support. He was interested in placing this device at a remote site, and creating a VPN tunnel back to the SonicWALL that we manage. I recommended that he purchase SonicWALL devices for each site (he had more that he wanted to set up), but he was not interested in forking over the thousands of dollars that it would cost him ... and I couldn't blame him.
I have created VPN's between all sorts of odd ball devices, so I didn't think that this one would be any different. Yet this Linksys device would turn out to have quite a few caveats, hence my documentation here.
Some things to know about these new Linksys VPN devices: They used an embedded version of OpenSWAN, they have been known to slack on standards (such as encryption key length), they are not at *all* supported by SonicWALL (probably because of the loose interpretation of standards), you *CANNOT* have spaces in your policy name (it will accept them, but your policy will be broken).
Now, onto the "how to". For this example, I was using a Linksys RVS4000 with Firmware Version: V1.0.11 (out of the box default stuff). The SonicWALL is a Pro 2040 running the latest enhanced firmware, 3.2.0.3e. Note: I did not upgrade the Linksys firmware as I should not be supporting that device at all. Additionally, I am doing all of it's configuration remotely. I would never *dare* update firmware on a device over the Internet (and neither should you).
The Linksys configuration will be a tad more complicated, so we will start with that. Our goal will be to match the settings of the SonicWALL so that the second part goes easier. I have tried all sorts of mis-matched settings, and some of them worked. But if you want this to go smoothly you should stick to what you see here. Go ahead and get logged into your Linksys (if you need help with this part, RTFM).
Once logged in, click VPN from the top, and then VPN Passthrough. We want to *disable* all of these options. This is enabled for people who want to use a remote VPN client from behind this device. We are going to terminate the VPN to this device itself, so we do not want or need any of this enabled. It would only confuse the Linksys. After you disable them, be sure to click the Save Settings button.
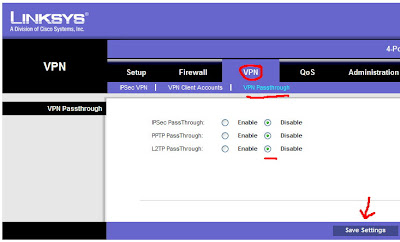
Next, also under VPN at the top, click "IPSec VPN". This will bring up a window that you have to scroll through to see all of the options. For tunnel entry it will read "new". We will start with a name. It's HIGHLY important that you NOT use any spaces here. I made this mistake, and it took me an hour or so of troubleshooting cryptic messages to figure it out. Linksys should *not* all you to enter spaces here, but they do.
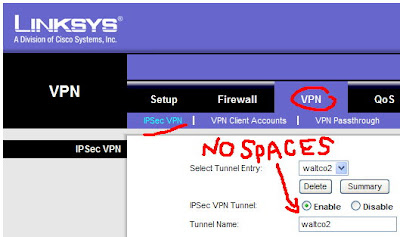
Keep scrolling and have a look at the other settings here. You can refer to this snapshot that I took.
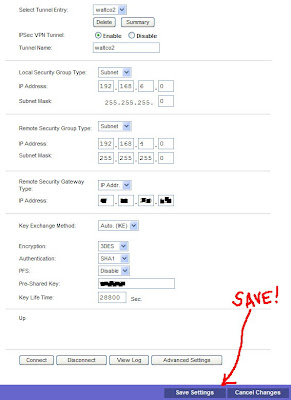
For this policy that I created, I used "Subnet" for both local and remote. This is usually what you are trying to accomplish. That is, you have two networks (must be different networks) and you want to allow traffic to pass between them. You can also create a "host to network" configuration where one computer accesses a subnet (or vice versa). Obviously, local network should be what is configured on the Linksys device. Remote network, is what the primary subnet is defined as on the SonicWALL side.
For the Remote Security Gateway, choose IP address and put in the static IP of the SonicWALL. If you SonicWALL does not have a static IP, you can pick the "any" option here. But that also means that you would need to later use "agressive mode" and change the "Local Identity" and "Remote Identity" to a "Name" under advanced settings. Hopefully you have a static IP. That makes things easy. :-) Make sure you enter the static IP of the SonicWALL!! Not the SonicWALL's gateway IP (people confuse what they want in this box).
For Key Exchange Method we want to leave it at Auto. Flipping over to manual unlocks a lot of options that I wouldn't want to try and match up to the SonicWALL. For Encryption choose "3DES" (you have no other choice). For Authentication pick "SHA1" as this is what the SonicWALL uses as default. Make sure you disable "PFS" (also default on the SonicWALL). For Pre-Shared key enter a secret word (feel free to use special characters here, it makes the encryption stronger). You will need this password later when you configure the SonicWALL side. Lastly, for Key Life Time enter "28800".
Before you do anything else find the Save Settings button at the bottom which is almost hidden in the colored bar. Save those settings, and then scroll back down to the bottom of the screen and click the "Advanced Settings" button. You will get a pop-up window, so turn off any stupid pop-up blockers that you may be using.
Here is a snapshot that you can follow along with ...
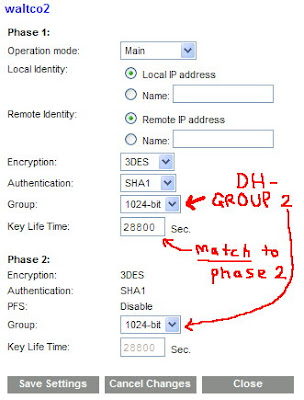
For your Operational Mode, you want to use Main Mode. That is, unless the other end is using a dynamic IP address (in which case you would use Aggressive). For the Local and Remote Identity boxes, leave them at the default settings. This is telling the Linksys that it will trust the SonicWALL's identity based on the IP address that it is connecting from.
For encryption, use "3DES" and change the Authentication to "SHA1". Trust me, life will be easier on you when it comes time to configure the SonicWALL. For the "Group" you want to pick "1024-bit". Most people would call this "DH Group 2" (like the SonicWALL will). Make sure you also change this Key Lifetime to 28800. We do this, because the SonicWALL is not that flexible on these options. Some devices offer a lot of options for keys and might even expire them based on the amount of data being transferred. Again, to make like easier ... just make this 28800 seconds. Lastly, click the "Save Settings" button. Then "Close" this window. You're done here.
For the SonicWALL side, get logged into your SonicWALL and select "VPN" on the left side. Then, click the Add button to get a new policy (otherwise called an "SA") started up. If you have trouble here, RTFM!
We will start with the first tab. Here is a snapshot to follow along with ...
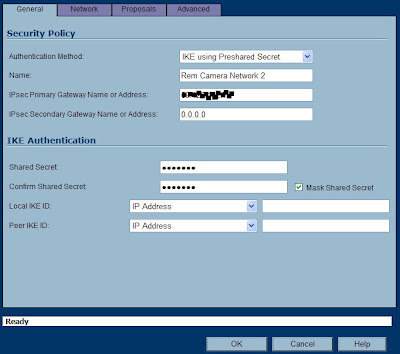
For Authenication Method, stick to the default. For name, pick whatever you want. If you are going to have a lot of these, you might want to pick a name that matches the Linksys at the other end. Or you can put something more meaningful here. SonicWALL will not punish you for using spaces. ;-)
For the IPsec Primary Gateway, enter the public IP address of the Linksys device. If it is using a dynamic IP, you can enter all zeroes here. Bear in mind, you would also have to change to agressive mode (at both ends) and use different "Local/Remote IKE ID" information. For the "Secondary" you can either enter zeroes, or let the SonicWALL do it for you. This field is in case you want to have a "failover" tunnel.
For the Shared Secret, enter the same Pre-Shared key that you used on the Linksys. This is your "secret word". Leave the Local and Peer IKE ID's alone (SonicWALL will know what to do here). Next, click the Network tab and have a look.
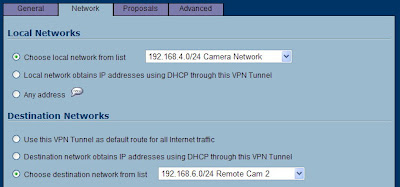
For the "Choose local network" you have some options here. If this is the only tunnel you will ever create, you can pick "LAN Primary Subnet". I have found that you can only use that object once in a policy, so I have got in the habit of making a new object that is a bit redundant. Click the drop down and choose "add network". I like to name it something meaningful such as use the network ID in the name, followed by a short description. Then if you have to look at this later, you will see the network ID right here in the policy. Now, make sure you create this is a "LAN" object, type is "Network". Enter the Network ID that this SonicWALL is configured for, and it's subnet mask. After you click "OK" you will be right back at this window.
For remote network, create a new network object that matches the Linksys. Your zone MUST BE "VPN" FOR THIS OBJECT. If it's not, this tunnel will not work!! Now you are ready to click the third tab "Proposals", and have a look.
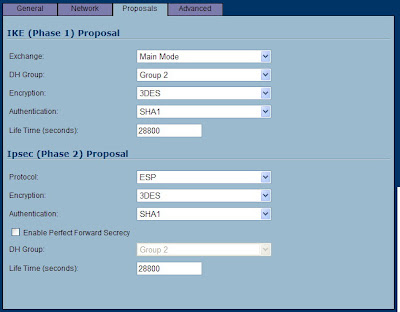
Now we can be glad that we made all those changes to the Linksys. For Exchange, leave it at "Main Mode" (unless you had to switch to aggressive). For DH Group, leave it at Group 2 (which means, 1024-bit on the Linksys). Use all of the other settings that we did on the Linksys: 3DES, SHA1 and 28800 seconds. For Phase 2, leave the default of ESP, 3DES, and SHA1. Also notice, the default Life Time is 28800 here, and PFS is Disabled! In essence, you should change nothing here, but make sure everything matches up.
Now clidk the Advanced tab. There are some things here you may need later. I don't like the thought of NetBIOS going over a routed network. Some folks might need that option though (for lousy name resolution or old network printing). Also, its a good idea to check the Keep Alive option ... but do that later. One of the lessons I have learned is that if you run a Keep Alive on a bad configuration, your log will fill up with a bunch of failed attempts. Rather, wait until this tunnel is coming up successfully and make a note to come back and add this option. The Keep Alive will maintain this tunnel even when there is no traffic running across it. I like to keep tunnels up all the time, so that when people need to send traffic across it - the tunnel is up and ready.
Now comes the fun part. Click OK on the SonicWALL policy to save it away. Note that it's all ready "Enabled". Watching this screen will get you nowhere. It does not refresh, ever. So head back over to the Linksys device now in a different tab/window - and click that Enable button at the bottom of the policy window. Now, on the SonicWALL you can click the VPN > Settings option on the left which will refresh this screen. Do you have a "green light" on the SonicWALL's policy? Does it show an active connection in the lower portion of the window? Great! No green light? You have problems ... keep reading.
Regardless of whether or not it worked, you had better read the logs. I find that the SonicWALL logs are far better (at least in this match-up). So click "Log" on the SonicWALL and see what you have. A successful policy would look like this ...
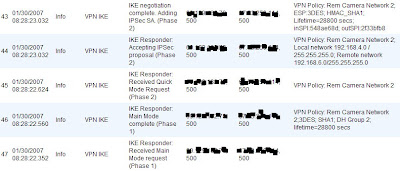
Note that the first line in the log, is the last thing that it recorded. Your policy notes should end with "Adding IPSec SA" as you see in the illustration. If it all looks well, try to run some traffic through the tunnel. Bear in mind, you cannot ping the internal interfaces of the two devices. That is, you cannot ping the Linksys's LAN IP from the SonicWALL (or vice versa). I'm really not sure why this is, but I think it may have to do with the way that these devices are terminating the tunnel from end to end. So instead, try getting onto a PC connected to one network and ping a PC at the other end. If that fails - check the logs for errors, and also remember to disable personal/Windows firewalls! ;-)
Troubleshooting/CaveatsI had some STRANGE problems when I first attempted this. I hope this helps someone out there.
1) The SonicWALL reports that the settings don't match, but they do! - I had the SonicWALL at one point tell me that the DH groups were different, when they were in fact matched. There was no convincing it otherwise, and the solution was to delete the policy, RESTART the SonicWALL, and start over. Don't waste your time trying anything else.
2) The tunnel is up, but traffic is not passing across it. - Check that the "remote" network on the SonicWALL side is configured as a "VPN" zoned object. You can find this setting in Network > Address Objects. If you accidentally made it a LAN or WAN object, you should go back to your policy, choose a different object (or create a new one) and name it something different. Then, go back and delete the one you made with errors.
3) The Linksys is not even starting the tunnel connection! - Did you put spaces in the policy name on the Linksys device? If you did, delete the policy and start over from scratch. Also check ALL of your settings and match them up. Look at the logs at *both ends* for clues, but know that the SonicWALL will be more helpful in determining the problem.
One thing I will say in favor of Linksys, their Log is "detachable" where SonicWALL keeps theirs glued down. What I mean is that you can create a Log "pop up" from the Linksys and keep that window aside while you troubleshoot. Here is how ...
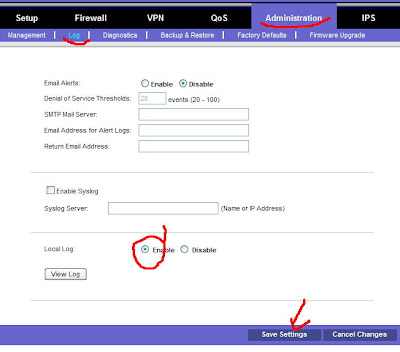
FIRST - Disabled your policy on the Linksys to stop it from logging junk. Then, click Administration > Log. You need to enable the Local Log as it is not turned on by default. Then make sure you Save Settings. Once that has been done, you can click the "View Log" button and you get a nice little logging window. It's not very big, and it doesn't refresh itself. So you will have to refresh it, and actually turn through the pages yourself. Also, the messages you will get will only make sense to someone who has worked extensively with OpenSWAN. Yet, pasting these errors in Google may uncover some good hints.
Once you have enabled your logging and you have your window up, go back and click "Enable" on the policy. Then refresh your log, and turn through the four or five pages of messages. Good luck!! ;-)
If you are attempting this and get stuck, feel free to comment, share your advice, point out my wrong doings, etc.
-Steve Ballantyne